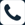Wallets
No matter which type of cryptocurrency you invest in, you’ll need to store the all-important private key information somewhere.
The “something” you store it in is a digital wallet, a must-have part of cryptocurrency investment. That “somewhere” can be online storage in a wallet or with a third-party storage service, called an exchange. Offline storage on paper or a hardware device are other (many say more prudent) alternatives.
Level of security risk. The longer that the device that stores your private key is connected to the internet, the higher the risk of losing your cryptocurrency investment.
- Hot wallets are stored at online exchanges and accessed with apps or a Web browser. They are “hot” because they are connected to the internet, which makes them more vulnerable to security breaches and malware attacks.
- Cold wallet is a method of storing coins offline (not connected to internet). This approach eliminates the opportunity for hackers to use an internet connection to break into a digital wallet and steal private key information.
- Hardware wallets are small cold wallet devices that often look like USB drives. They are physical storage devices you can use for cryptocurrency transactions. Each hardware wallet comes paired with a private key, which gives you access to the transaction validation data. Without access to the blockchain and its information, your coins are inaccessible.
- Paper wallets. This term describes the practice of writing private key information onto paper and storing it in a safe place offline.
Ideally, you would use two digital wallets, each for a different purpose. Use a hot wallet briefly to perform coin trades and transactions. Use the cold wallet (also known as cold storage) approach when you want to store your savings long-term.
Also, it’s a security best practice to back up both wallets’ private keys and store them offline in a safe place.
Cryptomining
When the first cryptocurrency system was set up and launched in 2009, it included a potential for up to 21 million bitcoins. Since then, only 17 million BTC are in use.
Cryptomining is the way that new cryptocurrency coins (also known as tokens) are released into circulation. The cryptomining process includes gathering and verifying recent transactions of bitcoin or other forms of cryptocurrency into blocks and adding them to the blockchain digital ledger.
The process requires miners to solve an extremely complex puzzle—whoever solves the puzzle first gets the coin. Staying competitive with other crypto miners, however, requires a computer with specialized hardware, lots of computer processing power and energy resources.
The opportunity for cryptomining fraud lies in:
- Hackers stealing coin directly from legitimate cryptomining companies.
- Tricking current or potential cryptominers to buying nonexistent computer hardware (phishing attacks).
- Cloud mining companies renting their equipment to cryptocurrency miners at prices higher than what they will actually earn. They provide “profits” by taking the coin’s value from new investors (equipment renters). This is a classic Ponzi scheme.
Cryptocrime Tactics
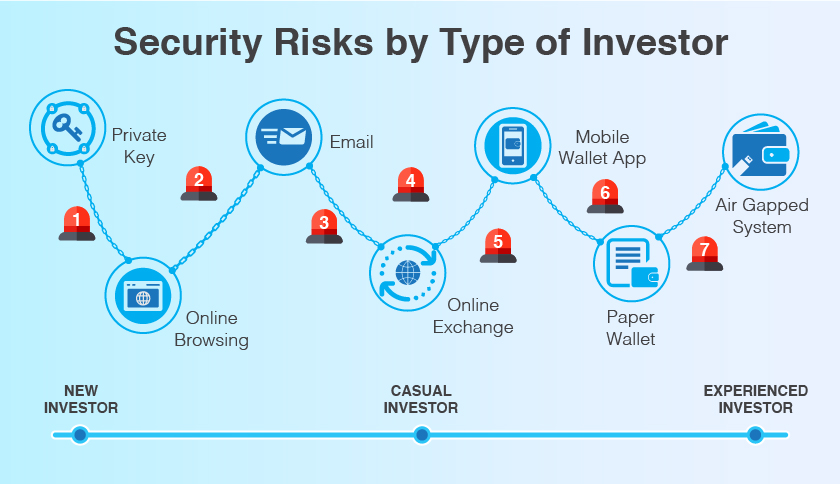
If you keep track of cryptocurrency technology and business news, you know there’s a long list of crimes, spoofs and shady dealings that relate to cryptocurrency. Here’s a list of terms to help you stay informed. How many do you recognize?
-
- Social engineering. This is a general term that describes a criminal entity fooling a target into doing something to the criminal’s advantage. Because social engineering is a means to an end, it is the prelude to other tactics such as ransomware or cryptojacking.
- Phishing. This tactic occurs when a criminal presents a target with a false pretext that can be a person, company, government agency or organization. In cryptocurrency investments, phishing attacks can progress to ransomware or various types of digital wallet break-ins that involve stealing credentials or private keys.
- Cryptojacking. This tactic involves diverting a target’s resources, without their permission. In cryptocurrency environments, cryptojacking usually involves diverting the computer CPU resources of coin holders to mine cryptocurrencies.
- Breaking into online wallets and exchanges. This tactic involves using different means (false identities in phishing attacks for example), to get private key information.
- Malvertising. The name tells the story. In this tactic, malicious ads are used to spread malware through criminally controlled online advertisements. The goal: to compromise web browsers and their plug-ins.
- ICO exit scams. Establish a new cryptocurrency. Publicize it and persuade investors to buy some. Reward folks who refer new investors with cash and tokens. Then, disappear. That’s the recipe of a standard initial coin offering (ICO) scam. If it sounds like a Ponzi scheme, you’re right.
- Poisoned website. This term describes a website that delivers malware as an ad on a website.
- Phone porting. This tactic is a wild mix of phishing, hacking and outright breaking and entering into wallets. Hackers snoop around social media, looking for cryptocurrency-related conversations, in which investors post their phone and email information. Then, posing as the victim, scammers call up the target’s phone provider. The goal: to fool the customer service representative into transferring the phone number to a device that the hacker controls.
- When the hackers take over the phone number, they can go into the victim’s cryptocurrency exchange account. They compromise the password and use the phone number for second-factor authentication. After that, it’s a matter of diverting investor funds to their wallets.
- Spear phishing. This is a focused phishing scam targeted at a specific person or organization. The phishing attack can precede data theft, or cybercriminals might use it to install malware on a target’s computer.
Securing Your Coin at Home and When You Trade
Some analysts consider offline (cold storage) wallets the only safe way to invest in cryptocurrency. If you’re talking about holding coin for the long term, offline storage is the safe way to go. But sooner or later, your coin must emerge from hibernation and be transferred to another wallet or an exchange.
Here are general tips that will help you keep your coin safe, wherever it might be.
Isolate Your Investment
There are ways to keep your coins safe, when you store them at home or transfer them during a transaction.
When security measures refer to using a dedicated computer—one that only transfers cryptocurrency into and out of a digital wallet—the computer is protected by an air gap. This security measure refers to computers or networks that are not connected directly to the internet or to any other computers that are connected to the internet.
Securing your coin this way is a simple process. You connect the (ideally new and unused) computer to the internet, complete the cryptocurrency transaction, disconnect the computer from the web immediately and use it for nothing else—ever.
Protect Yourself When You Trade Cryptocurrency
In addition to the isolation methods described above, use these tactics when you move coin into or out of your digital wallet:
- Secure your operating system. Install it on a new computer or scrub your hard drive and reinstall your OS on a machine you already own.
- Find and use a good password manager. It’s easy to mistype private keys, which can be more than 50 characters long. No one is perfect. Buy a memory aid and sleep soundly. See here.
- Use two-factor authentication on every device that transfers or accepts cryptocurrency. See here.
- Get an offline (hardware) wallet. It’s the safest way to hold your investment between transactions. See here.
- Use a virtual private network (VPN) whenever you authorize the transfer of cryptocurrency-related information. VPNs encrypt the network path between your coin and its destination.
It’s always a good idea to use a VPN whenever you’re on a coffee shop or other network that you don’t control.
Facing the Challenge of Cryptocurrency Security
Bitcoin stands out as the oldest and the most successful cryptocurrency. But, a wide range of security concerns about BTC is emerging, because it’s vulnerable to illegal transactions or attacks within online storage pools and exchanges.
The Bitcoin protocol we know today was built on the proof-of-work principle, in which transactions can be processed securely on a decentralized, peer-to-peer network. But, without a central collection institution such as a bank, cryptocurrency mining and transaction processes are not entirely secure.
Stay Alert, Get Educated
As you read through the how-to descriptions below, stay alert to methods that require technical knowledge or abilities. Then get educated (or engage an experienced security specialist). You don’t have to be a tech wizard to protect your cryptocurrency. There are no guarantees, but the more security awareness you develop, the lower your risk of something going wrong.